
Title: A Survey on Active Packets in Active Networks
email: mailto:nbantan@cs.kent.edu, homepage: http://www.aegis.mcs.kent/~nbantan
Prepared for Prof. Javed I. Khan
Department of Computer Science, Kent State University
Date: November 2001
Abstract: A new way of thinking about the role of network
packets must invoked. Active packet produces such mindset where network
packet will decide on their fate. Active packets can invoke a program at
its destination in the physical layer. This invocation will balance the
processing of the transfer data between routers and host machines(computes)
Other
Survey's on Internetwork-based Applications
Back to Javed I. Khan's Home
Page
Table of Contents:
Introduction
Active network components
Active Packets
PLAN
ANTS
General Active Packet Processing
Active Packets Control
Characterizing Active Packets
Conclusion
References
Research Groups
Other Relevant Links
Introduction:
What is Active Network?
New applications continue to emerge rapidly and often
benefit from new network services that better accommodate their modes of
use. Active Network recoups network services from the underlying hardware
and by allowing new services to be demand loaded into the infrastructure
[TGSK96]. Implementing them at nodes interior to the network or at the
network layer often offers better functionality and performance. Active
network permit applications to support faster service innovation by making
it easier to deploy new network services which has a potential impact of
active network services on application and how such services can be built
and how such service can be built and deployed [WeLG98]. Also, Active
networking allows customized packet processing inside the network on a
per-packet, per-flow, or per-service basis [HiMA99].
From the management perspective, active networking
technology facilitates rapid service deployment and flexible service management
in which dynamically generating fast path programs that streamline the
execution of the most common packets. Active networks will leverage middleware
services that support the coordination of network management functions,
such as the installation of new software and hardware, load balancing,
fault tolerance, accounting and auditing, [TGSK96].
Furthermore, users can "program" the network, by supplying their own
programs to perform computations according to their need. Active networks
will allow users to deploy new services by tailoring components of the
shared infrastructure to suit their requirements. For example, users could
request that a router execute an application-specific compression algorithm
during the processing of their packets [TGSK96]
Active
network components
Active Packets
The projects, which we will discuss in this survey, are:
- Smart Packets
- PLAN
- ANTS
SMART Packets
The Smart Packets architecture consists of four parts:
1-A specification for smart packet formats and their encapsulation into some network data delivery service.
2-The specification of a high-level language, its assembly language, and a compressed encoding representing that portion of a smart packet that gets executed.
3-A virtual machine resident in each networking element to provide a context for executing the program within the smart packet, and
4-A security architecture.
Users inject programs contained in messages into an active network. Routers along the network receive these messages, execute the programs within, and (possibly) return values or forward the messages along to other routers [SJS+00]. The program seeks to increase user and application control over how packets are handled, and to increase the flexibility of computer networks and the ability to upgrade them.
Packets has a few requirements:
- Transport service should be connectionless;
- Fragmentation of is not permitted.
- Each program must be under 1KB in length.
- There should be a virtual machine used to provide surety of safety while executing the program.
- Remote execution of code must be done in an insular environment.
User-written network management and monitoring programs generate smart packets—encapsulated in Active Network Encapsulation Protocol (ANEP) [Alexander et al. 1997] frames—and give them to the ANEP Daemon process. The ANEP Daemon process has two responsibilities:
- It is the injection and reception point for smart packets,
- It also contains the virtual machine for executing the programs received.

Figure 1. IP and ANEP encapsulation
A smart packet consists of a Smart Packets header followed by payload. The smart packet is encapsulated within an ANEP packet, which, in turn, is carried within IPv4, IPv6, or, in some Active Networks tests bed situations, UDP. For a smart packet, however, the router must process the contents of the datagram before forwarding it. As a further complication, the router should examine the contents of the datagram only if the router supports Smart Packets. Otherwise, the router should pass the datagram through by modifying an IP option
Smart packets contain either a program, resulting data, or messages wrapped within a common Smart Packets header and encapsulated within ANEP. The Program Packet carries the code to be executed at the appropriate hosts. The Data Packet carries the results of the execution back to the originating network management program. The Message Packet carries informational messages rather than executable code. Error Packets return error conditions if the transport of a Program Packet or the execution of its code encounters exceptions. Only Program Packets use the IP Router Alert option.
When a Program Packet arrives at a router, the daemon authenticates the identity of the sender, verifies the data origin and data integrity, and checks if the sender is authorized to run the smart packet’s program. Then an instance of the virtual machine is instantiated, and the code within the packet is executed.
As part of the security architecture, the virtual machine is made aware of resource limits such as maximum number of instructions to be executed, and how much memory can be used, and privileges such as whether access to MIB sets is allowed.
PLAN
The primary component of each packet is its chunk
(short for code hunk), which consists of code, a function name to serve
as an entry point, and values to serve as bindings for the arguments of
the entry function.The other components
are the destination address, the global resource bound (a counter), the
routing function, the source address, and the function for error handling.
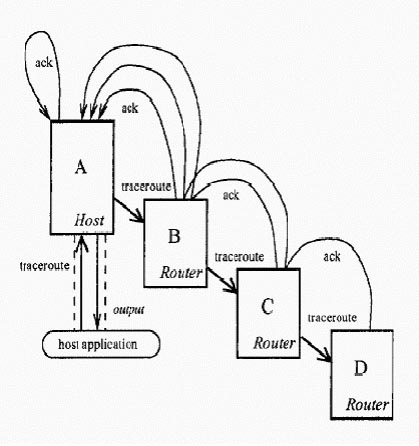
Figure 2. An example of PLAN packet journey (traceroute packet).
A host application constructs a PLAN packet and injects it into the active network via a port connected to the local PLAN interpreter. This injection port is used by PLAN to provide output to the application, and allows the application to create new packets. Once a packet is created, it is sent to its destination for evaluation. If the destination is many hops away, so intermediate nodes need a way to determine the ‘next hop.’ This is done using the packet’s routing function field, which names a service function that takes the destination as an argument and returns the next hop towards that destination. At each hop, the resource bound field is decremented by one; if the resource bound is exhausted, the packet is terminated.
Specific components of PLAN:
- PLAN has simple flow of control constructs (statement sequencing, conditional execution, iteration over lists with fold, and exceptions)
- PLAN has No recursion and unbounded iteration
- All PLAN programs terminates
- PLAN has an exception handler
- PLAN is strongly typed,
- PLAN is lexically scoped, with the available services occupying the initial bindings in the namespace.
- PLAN programs can only share state through service routines,
The PLAN programming environment is used to build an active internetwork, PLANet. PLANet’s basic protocols are based on ones used in IP, but with a key difference: all packets are PLAN programs. In PLANet, distributed protocols used to maintain the network, such as routing and address resolution protocols, are implemented as a combination of PLAN programs and services [HKM+98].
PLAN is implementation
When choosing an, we had several specific requirements. First, to make the claim that the network is programmable,
The implementation language for PLAN must be
1-Dynamically loadable,
2-Easily portable, and
3-Strongly typed.
The authors chose OCaml [Caml] and the Pizza [Pizz] extension to Java [GoJG96].
ANTS
Each capsule consists of the following:
- Identifier for its protocol
- Capsule type
- A shared header (common fields to all capsules.)
- Payload
Capsules are like mobile agents in that they direct themselves through the network by using a custom forwarding routine. The type of forwarding is indicated by the value of the type field and is selected by end-user software when it injects a capsule into the network. The corresponding forwarding routine is transferred using mobile code techniques to active nodes that the capsule visits as it passes through the network. The routine is executed at each active node that is encountered along the forwarding
Path. At conventional nodes, IP forwarding occurs using the IP header fields.
ANTS do not restrict who can program which nodes. Instead, ANTS aims to allow each user to construct new data transfer services across the wide-area, such as routing for host mobility, by controlling the handling of their own packets. Within the network. This is analogous to extensible operating system approaches that aim to offer entrusted applications as much control over the way system resources are managed as possible while still being able to protect the underlying resources and arbitrate between competing demands. ANTS is based on an aggressive “capsule” approach in which code is associated with packets and run at selected IP routers that are extensible. We sketch its design in the following [Weth99]:
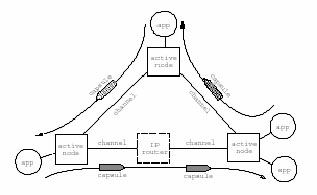
Figure 3. ANTS entities
The entities in an ANTS network are shown in Figure 3. Applications obtain customized network services by sending and receiving special types of packets called capsules via a programmable router referred to as an active node. Each active node is connected to its neighbors, some of who can be conventional IP routers, by link layer channels. The innovative properties of an ANTS network stem from the interaction of capsules and active nodes; the application and channel components are simply modeled on those of conventional networks.
The first step is to write a new set of forwarding routines that implement the desired behavior. This is done in a subset of Java in our reference implementation, the ANTS toolkit. Each different forwarding routine corresponds to a different type of capsule and can carry different header fields. The kinds of forwarding routines that can be constructed depend on the capabilities of the active node; routines are further restricted in the amounts of node resources they can consume.
It provides three categories of calls that: query the node environment; manipulate a soft-store of service-defined objects that are cached for a short time and then expired; and route capsules towards other nodes or applications in terms of shortest paths. Once the code is written, it is signed by a trusted authority (an IETF-equivalent) to certify that the service makes use of overall network resources in a “reasonable” fashion. Finally, the code is registered with a directory service using a human-readable name to make it available to other network users.
General Active Packet Processing
The general flow of the packets through an active node is shown in figure 2. When

Figure 4: Packet flow through an active node.
When a packet is received on a physical link, it is first classified based on information in the packet (i.e. headers); this classification deter-mines the input channel —including protocol processing— to which the packet is directed. Classification of incoming packets is controlled by patterns specified by the EEs.
After input channel processing the packet is handed off to the EE that requested creation of the channel.
It is the responsibility of the NOS and security engine to ensure that the requesting principal is permitted access to the set of packets implied by the pattern associated with a channel creation request. Incoming packets that match no pattern are dropped.
On the output side, EEs transmit packets by submitting them to output channels, which include protocol processing as well as output scheduling. Thus, the general progression is link input, classification, input protocol processing, EE/AA processing, output protocol processing, scheduling, and link transmission. Each transmitted packet corresponds to some received packet; EEs may aggregate or generate them spontaneously [Calv99].
Active Packets Control
The Active Network Encapsulation Protocol also provides a vehicle for other communications with the NOS, including:
- Error-handling instructions. When a packet fails to reach the desired EE at a node, the ANEP header lets the user instruct the Node OS as to the expected response, (e.g. drop the packet silently, try to forward it, or send an error message).
- Security vouchers. It is impractical for every node in the network to retrieve or store the information required to authenticate every packet passing through it. However, it may be practical for a packet to be authenticated just once when it enters the network.
- Fairness: Control of the unfairness is accomplished via QoS specifications, which are ultimately realized as queuing disciplines. The queuing disciplines use packet discrimination to apply the policy resulting from a QoS specification. A concrete example of an applied queuing discipline (e.g., Weighted Fair Queuing or Virtual Clock) is allocating bandwidth to flows in an IP Internet, or allocating a more complex resource profile (memory, CPU, input/output port bandwidths) in an active network [AAK+99].
Characterizing Active Packets
- Safety: preventing outages caused by malicious or incorrect packet programs
- Efficiency: providing acceptable performance; and
- Flexibility: providing a wide range of programmable functionality.
Safety: We define the safety of an active packet system as the degree to which it protects the overall network from attack or misuse, whether deliberate or accidental. We contend that an active packet system should strive to provide at least the level of safety of IP. Failure to do so would be a very sizeable barrier to deployment in the Internet. Ideally, an active packet system should provide an even higher level of safety than IP.
Efficiency: We define the efficiency of an active packet system as the ratio of network work performed (perhaps in terms of bandwidth, or packets processed) to CPU cycles used. IP provides us with a natural reference point for efficiency; we expect most active packet systems to be less efficient than IP. We draw a distinction, however, between efficiency and performance.
Flexibility: We define the flexibility of an active packet system as the amount of new functionality made possible by the system as contrasted to IP. It may be the case that it is hard to compare the flexibility of any two active packet systems, so our discussion of related work in Section 3 will be a partial ordering of the systems in question.
The following table illiterate the degree of each characterization on each project.
|
|
Safety
|
Efficiency
|
Flexibility
|
|
Smart Packets
|
To control network-wide resource use, ANTS provides
a TTL field, which is decremented at each hop, and duplicated when packets
create a child packet. Since packets can create any number of child packets,
the TTL limits the distance a packet’s children can travel, but not the
total work in the network. Currently ANTS requires that some authority
certify capsules before being deployed to limit the possibility of malicious
packets. This significantly reduces the speed at which new capsule programs
can be deployed, and of course raises the question of the correctness of
the certification.
|
However, Wetherall argues that capsules in a given
network flow will likely require similar processing, so at 16 Mbps for
the in-cache case, this early ANTS prototype already achieves performance
adequate to T1 line rates [Moor99].
|
There could be multiple copies of the same code
residing in a given cache, which would be problematic if a proliferation
of application protocols resulted in widespread cache contention.
|
|
PLAN
|
Network bandwidth is governed by a strictly decreasing
resource bound carried by each packet. When a packet spawns a child
packet, it must donate some of its remaining resource bound to the child,
thus bounding the total number of network hops which a packet and its descendants
can take. Unfortunately, it is difficult to know how to set this bound,
and there is currently no provision for preventing the bound being set
unreasonably high when the packet is first injected. Finally, PLAN’s service
namespace may be dynamically restricted or expanded based upon cryptographic
credentials [MoNe01].
|
The main savings here was being able to avoid packet-marshalling
costs on the routers where PLAN evaluation did not occur. The main overheads
identified in PLANet were kernel crossings, thread scheduling, and garbage
collection.
|
One awkward point, however, is that the resource
bound conservation properties make it difficult (from programmer’s point
of view) to apportion a packet’s resource bound among multiple children.
|
|
ANTS
|
These certificates may be omitted, in which case
the packet runs in a very resource-limited environment that is nonetheless
sufficient to perform simple diagnostic functions such as ping or
traceroute.
|
Smart Packets may nonetheless be fast enough. Unfortunately,
basic performance numbers are not available at this time.
|
Providing MIB operations means that Smart Packets
should be able to perform most SNMP-style management tasks.
|
Active Packets Application
- Multimedia application benefit fro real-time and multicast services and IP Multicast [Murp97] reduces the bandwidth needed to communicate from one sender to multiple receivers. Excess bandwidth and latency costs are incurred when an overlay is used and its topology does not match the underlying topology.
- Laptops benefit from host mobility and transport services optimized for wireless transmission
- Web servers benefit fro caching and load distributing services [WeLG98].
- Web proxies are an application-specific service interposed between clients and browsers. Using the ActiveNet, this system could be extended, allowing nodes of the hierarchy to be located at strategic points within the network [TGSK96].
Conclusion
The PLAN project attempts to address safety concern via language design. The PLAN packet language has limited expressivities, so that authentication is not required to execute packet programs. Notably, all PLAN program are guaranteed to terminate [Moor99]. ANTS packets add extensibility at the network layer and allows for incremental deployment of active nodes within the internet. ANTS tackles the challenges of ensuring that the flexibility offered by active networks does not adversely impact performance or security.
References
Research
Papers for More Information on Active Packet/Active Network.
D. Scott Alexander, William A. Arbaugh, Angelos D. Keromytis, Steve Muir
and Jonathan M. Smith. Secure Quality of Service Handling (SqoSH),
IEEE Communications Magazine . April 2000. http://citeseer.nj.nec.com/311767.html
M. Brunner, B. Plattner, R. Stadler, Service Creation and Management in Active Telecom Environments. Communications of the ACM, April 2001. http://www.tik.ee.ethz.ch/~brunner/papers/CACM_Camera_Ready_final.pdf
K. L. Calvert. Architectural framework for active networks, version 1.0, University of Kentucky, July 1999. http://www.dcs.uky.edu/~calvert/arch-latest.ps
Caml home page. http://pauillac.inria.fr/caml/index-eng.html.
James Gosling, Bill Joy, and Guy Steele. The Java Language Specification. Addison Wesley, 1996. http://java.sun.com/docs/books/jls/
Michael Hicks, Jonathan T. Moore, and D. Scott Alexander. PLANet: An Active Internetwork. In IEEE Intl. Conf. On Computer Communications (INFOCOM '99), pages 1124--1133, 1999. http://citeseer.nj.nec.com/hicks99planet.html
J. T. Moore. Safe and efficient active packets. Technical Report MS-CIS-99-24, Department of Computer and Information Science, University of Pennsylvania, October 1999, http://citeseer.nj.nec.com/moore99safe.html
J. Moore and S. Nettles. Towards Practical Programmable Packets. Proceedings of the 20th Conference on Computer Communications (INFOCOM). IEEE, Anchorage, Alaska, April 2001. http://citeseer.nj.nec.com/294052.html
David Murphy, Building an Active Node on
the Internet. Technical Report MIT-LCS-TR-723. Master of Engineering
thesis, May 1997. http://citeseer.nj.nec.com/murphy97building.html
Pizza home page. http://pizzacompiler.sourceforge.net/
Beverly Schwartz and Alden W. Jackson and W. Timothy Strayer and Wenyi Zhou and R. Dennis Rockwell and Craig Partbridge. Smart packets: applying active networks to network management. ACM Transactions on Computer Systems. Volume 18, number 1, pages 67--88, 2000. http://citeseer.nj.nec.com/schwartz00smart.html
D.L. Tennenhouse, S.J. Garland, L. Shrira, and M.F. Kaashoek. From Internet to ActiveNet. Request for Comments, January 1996. http://citeseer.nj.nec.com/tennenhouse96from.html
D. L. Tennenhouse, J. M. Smith, W. D. Sincoskie, D. J. Wetherall, and G. J. Minden. A survey of active network research. IEEE Communications Magazine, pages 80--86, January 1997. http://citeseer.nj.nec.com/tennenhouse97survey.html
David Wetherall. Active network vision and reality: lessons form a capsule-based system. Symposium on Operating Systems Principles, pages 64-79,1999. http://citeseer.nj.nec.com/wetherall99active.html
David J. Wetherall, Ulana Legedza, and John Guttag. Introducing New Internet Services: Why and How. IEEE Network Magazine. July/August 1998. http://www.sds.lcs.mit.edu/publications/network98.html
M. Hicks, P. Kakkar, J. T. Moore, C. A. Gunther, and S. Nettles. PLAN: A Packet Language for Active Networks. In Proceedings of the Third ACM International Conference on Functional Programming Languages (SIGPLAN'98), pages 86-93, May 1998. http://citeseer.nj.nec.com/hicks98plan.html
Research
Groups
Active Network is an ongoing project that is taking place in many universities
and laboratories. MIT has a special groups dedicate for this research.
They can be reached at this location http://www.sds.lcs.mit.edu/activeware/
Other
Relevant Links
- Active and High Confidence Networks, BAA-9704 from DARPA
- Liquid Software at Arizona
- SwitchWare at UPenn and Bellcore
- NetScript at Columbia
- Active Networking at Georgia Tech
- Smart Packets at BBN